I have read this article which talks about adding custom field (email confirmation for 2nd time) in the Self Registration page. The scenario is simple:
To add field Confirm Email for 2nd time in the Self Registration page. This behavior can been seen in many of the websites. So, what would you do when you are using OIM for this purpose? By default, OIM supports adding custom fields to custom self registration page by modifying the FormMetaData.xml file. However, the problem arises when you want to add logic to the form to have the Email confirm field match the Email field. This can be done easily (either by adding javascript or by adding custom code) if it is a custom Self Registration Page and not OIM self registration page. The workaround is so simple: Decompile the tcSelfRegistrationAction.class java file deployed in the XellerateFull.ear file and copy the function of confirming the password and change the field name to email.
Mahendra Krishnapatnam is a cybersecurity expert and technology thought leader with extensive experience in identity and access management (IAM), cloud security, and AI-driven threat mitigation. He actively contributes to research, mentors startups, and serves as a judge for global cybersecurity and technology awards. His work bridges innovation and impact across healthcare, finance, and public sector domains.
Monday, November 8, 2010
Sunday, November 7, 2010
Identity propogation in a flow involving OAM, OWSM and OSB
I have recently gone through this article and found very interesting.
The scenario is this:
OAM is protecting a Portal UI application which is making WebService calls. WebService is protected by OWSM and the communication is made through OSB. Two approaches were discussed in detail in that article.
The scenario is this:
OAM is protecting a Portal UI application which is making WebService calls. WebService is protected by OWSM and the communication is made through OSB. Two approaches were discussed in detail in that article.
Friday, October 29, 2010
Performance tuning of Oracle Access Manager
I am glad that I got an opportunity to perform the tuning process of a real time IAM project implementation.
This is one area which I found very interesting and challenging.
Well, I would like to talk & give directions about various tuning aspects of Oracle Access Manager.
The Oracle Access Manager deployment guide and sizing guide (also called capacity planning) are references for this.
The tuning process has to be in the following order:
This is one area which I found very interesting and challenging.
Well, I would like to talk & give directions about various tuning aspects of Oracle Access Manager.
The Oracle Access Manager deployment guide and sizing guide (also called capacity planning) are references for this.
The tuning process has to be in the following order:
- Tuning the Database: In my case, we have used Oracle database and tuning guide is here.
- Tuning the LDAP: In my case, we have used Oracle Internet Directory as user store. OID tuning guide is here. No matter how well you tune the Oracle Access Manager, it makes to trip to LDAP for authentication and authorization calls. So, it is vital to tune the LDAP prior to Oracle Access Manager.
- Tuning the Web Server: Oracle Access Manager web components such as webpass and webgate webserver components has to be tuned well. In my case, we have used OHS WebServer (tuning documentation) and Apache WebServer (tuning documentation) for webgates and webpass components.
- Tuning the Oracle Access Manager: Components to be tuned here are Identity System and Access Server.
- Tuning the network: The performance of the overall network, or network latency, is a major factor in the performance of the system. A reduction in network latency will be reflected in the performance of Oracle Access Manager. Documentation is here.
Thursday, October 21, 2010
Things to remember for integrating BPEL worklist with OSSO in realtime
I have written a post earlier on the integration aspects of OSSO with BPEL worklist. However, I did not talk about real time aspects of this integration. Let's assume there are 2 nodes of OSSO servers with software load balancer (with virtual hostname say osso.oracle.com) configured in the production system. In the same lines, let's assume there are 4 nodes of BPEL worklist with hardware loadbalancer (with virtual hostname say soa.oracle.com).
The first step of this integration is to register the BPEL worklist as a partner application to OSSO server using ssoreg.sh script. The question is on how many OSSO nodes will we run this script? The answer is single node. Since the OSSO servers are clustered, registering in one node will automatically get reflected in another node. However, a small additional step needs to be performed i.e., osso.conf file generated in first node has to be copied to the 2nd to the same location say $ORACLE_HOME/Apache/Apache/conf/osso/worklist. Remember that while running the ssoreg.sh script, the hostname specified for the middle tier i.e., SOA worklist is the Virutal hostname instead of individual server hostname.
To verify, login to OSSO console and check whether the application is registered or not.
Next step is the configuration part at the BPEL end using the metalink note 753087.1.
The question is whether to perform this configuration part at single node of BPEL server or all the nodes? The answer is all the nodes.
Please reach out to me in case of any doubts.
The first step of this integration is to register the BPEL worklist as a partner application to OSSO server using ssoreg.sh script. The question is on how many OSSO nodes will we run this script? The answer is single node. Since the OSSO servers are clustered, registering in one node will automatically get reflected in another node. However, a small additional step needs to be performed i.e., osso.conf file generated in first node has to be copied to the 2nd to the same location say $ORACLE_HOME/Apache/Apache/conf/osso/worklist. Remember that while running the ssoreg.sh script, the hostname specified for the middle tier i.e., SOA worklist is the Virutal hostname instead of individual server hostname.
To verify, login to OSSO console and check whether the application is registered or not.
Next step is the configuration part at the BPEL end using the metalink note 753087.1.
The question is whether to perform this configuration part at single node of BPEL server or all the nodes? The answer is all the nodes.
Please reach out to me in case of any doubts.
Wednesday, October 20, 2010
How to start EM Console service explicitly?
Enterprise Manager console is the basic console to perform the health checkups, check ports and so on for Oracle Application Server. One of the easiest way to access the EM console (if you dont know the exact URL or port number) is by accessing the HTTP Server home page and clicking the Login to IAS Admin Console link. If the EM console is not started then you will see Page cannot be displayed error.
Now, you can check the status of the EM console using the command ./emctl status iasconsole (Execute this command in the location $ORACLE_HOME/bin) - This is for LINUX system
If it is not started, use this command to do so ./emctl start iasconsole and the output will be shown as below.
[oracle@hostname bin]$ ./emctl start iasconsole
TZ set to Asia/Calcutta
Oracle Enterprise Manager 10g Application Server Control Release 10.1.4.3.0
Copyright (c) 1996, 2006 Oracle Corporation. All rights reserved.
http:// hostname:7018/emd/console/aboutApplication
Starting Oracle Enterprise Manager 10g Application Server Control ...... started successfully.
[oracle@hostname bin]$
Now, you can check the status of the EM console using the command ./emctl status iasconsole (Execute this command in the location $ORACLE_HOME/bin) - This is for LINUX system
If it is not started, use this command to do so ./emctl start iasconsole and the output will be shown as below.
[oracle@hostname bin]$ ./emctl start iasconsole
TZ set to Asia/Calcutta
Oracle Enterprise Manager 10g Application Server Control Release 10.1.4.3.0
Copyright (c) 1996, 2006 Oracle Corporation. All rights reserved.
http:// hostname:7018/emd/console/aboutApplication
Starting Oracle Enterprise Manager 10g Application Server Control ...... started successfully.
[oracle@hostname bin]$
Integration of E-Business Suite 12.x with Oracle Single Sign-on Server 10.1.4.3 in real time
Not many people talk about real time aspects of any integrations and the configurations involved. However, I would like to bring a small point which is vital for integrating E-Business Suite 12.x with Oracle Single Sign-On Server 10.1.4.3.
Lets assume E-Business suite is running on 2 nodes and OSSO server on 2 other nodes (nodes imply different machines or different instances in same machine) in production mode. In real time mode, you will be accessing the OSSO server console/application using a virtual hostname (instead of individual hostname) and same is the case for E-Business suite. For integrating OSSO with E-Business Suite, we will run a perl script txkrun.pl which registers E-Business Suite as partner application in OSSO server. The question is whether to run the script in both nodes of E-Business suite or just single node. The answer is single node as the script will pick up values from profile options that are in the database (A person called Atul helped me in this concept).
The runtime inputs to be provided for the perl script txkrun.perl is shown below:
$FND_TOP/bin/txkrun.pl -script=SetSSOReg
Lets assume E-Business suite is running on 2 nodes and OSSO server on 2 other nodes (nodes imply different machines or different instances in same machine) in production mode. In real time mode, you will be accessing the OSSO server console/application using a virtual hostname (instead of individual hostname) and same is the case for E-Business suite. For integrating OSSO with E-Business Suite, we will run a perl script txkrun.pl which registers E-Business Suite as partner application in OSSO server. The question is whether to run the script in both nodes of E-Business suite or just single node. The answer is single node as the script will pick up values from profile options that are in the database (A person called Atul helped me in this concept).
The runtime inputs to be provided for the perl script txkrun.perl is shown below:
$FND_TOP/bin/txkrun.pl -script=SetSSOReg
Enter the host name where Oracle iAS Infrastructure database is installed ? Virtual Hostname of OSSO Server (not to get confused as it specifies Infrastructure database hostname)
Enter the LDAP Port on Oracle Internet Directory server ? 389 (default port is 389, if you have customized the ports, then specify it)
Enter SSL LDAP Port on Oracle Internet Directory server ? 636 (default port is SSL, if you have customized the ports, then specify it)
Enter the Oracle Internet Directory Administrator (orcladmin) Bind password ? (OID administrator password)
Enter the instance password that you would like to register this application instance with ? (mostly this password is same as OID admin password)
Enter Oracle E-Business apps database user password ? (EBS apps user password)
Enter the LDAP Port on Oracle Internet Directory server ? 389 (default port is 389, if you have customized the ports, then specify it)
Enter SSL LDAP Port on Oracle Internet Directory server ? 636 (default port is SSL, if you have customized the ports, then specify it)
Enter the Oracle Internet Directory Administrator (orcladmin) Bind password ? (OID administrator password)
Enter the instance password that you would like to register this application instance with ? (mostly this password is same as OID admin password)
Enter Oracle E-Business apps database user password ? (EBS apps user password)
Labels:
E-Business Suite,
Integrations,
OSSO
Sunday, October 10, 2010
Configuring Oracle Access Manager 11g
This post covers the Configuration part of Oracle Access Manager 11g. To know about installing and configuring the Oracle Identity and Access Management 11.1.1.3, check the previous post .
Configuring Oracle Access Manager 11g contains the steps for creating a WebLogic domain which has OAM Admin Server, EM consoles etc., deployed in WebLogic server.
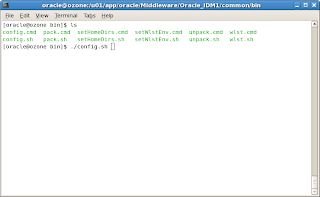
First step is to run the config.sh present in the location/common/bin.
 We are just configuring the OAM alone, hence we have selected Oracle Access Manager with Database Policy Store.A database policy store offers more security measures that can be layered based on the storage, thereby ensuring higher resiliency to corruption and better high availability. We have also selected Oracle Enterprise Manager here.
We are just configuring the OAM alone, hence we have selected Oracle Access Manager with Database Policy Store.A database policy store offers more security measures that can be layered based on the storage, thereby ensuring higher resiliency to corruption and better high availability. We have also selected Oracle Enterprise Manager here.
Specify a Domain name.
Specify the weblogic user password.
Specify the Service Name of the database, database hostname, database port. Select the OAM Infrastructure component for configuring the JDBC schema.
Test the JDBC connection.
Access the WebLogic administration console, http://host:port/console
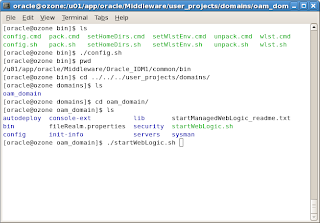
Start the OAM Access Server, run startManagedWebLogic.sh with parameter as oam_server1 as shown below.
Access the OAM console using http://host:port/oamconsole. Login as weblogic user.
This completes the OAM Configuration and now you can play with this product.
Configuring Oracle Access Manager 11g contains the steps for creating a WebLogic domain which has OAM Admin Server, EM consoles etc., deployed in WebLogic server.
First step is to run the config.sh present in the location

Note:
When you select the Oracle Access Manager with Database Policy Store - 11.1.1.3.0 [Oracle_IDM2] option, the Oracle JRF - 11.1.1.0 [oracle_common] option is also selected, by default.Specify a Domain name.
Specify the weblogic user password.
Specify the Service Name of the database, database hostname, database port. Select the OAM Infrastructure component for configuring the JDBC schema.
Test the JDBC connection.

Start the WebLogic admin server using startWebLogic.sh present in the location Oracle_Home/user_projects/domains/oam_domain
Access the WebLogic administration console, http://host:port/console
Start the OAM Access Server, run startManagedWebLogic.sh with parameter as oam_server1 as shown below.

Access the OAM console using http://host:port/oamconsole. Login as weblogic user.
This completes the OAM Configuration and now you can play with this product.
Saturday, October 9, 2010
Installing Oracle Identity and Access Management Suite 11.1.1.3.0
I have covered the installation part of Oracle Identity and Access Management suite 11.1.1.3.0 with screenshots.
The pre-requisites before installing this product are:
If you want to install only Oracle Identity Manager Design Console or Remote Manager, you do not need to install Oracle WebLogic Server or create a Middleware Home directory on the machine where Design Console or Remote Manager is being configured.
Now, let us proceed with installation screens directly.
Let us see the folders that gets created in Oracle Home location.
A folder called Oracle_IDM1 gets created and this is the IDM home.
Next step is to configure the Oracle Access Manager by creating WebLogic domain which will be covered in a seperate post.
The pre-requisites before installing this product are:
- WebLogic Server 10.3.3 should have been installed.
- Oracle Database above 11.1.7.0+ or 11.2.x should have been installed
- Created schema for Oracle Access Manager using RCU.
If you want to install only Oracle Identity Manager Design Console or Remote Manager, you do not need to install Oracle WebLogic Server or create a Middleware Home directory on the machine where Design Console or Remote Manager is being configured.
Now, let us proceed with installation screens directly.
Let us see the folders that gets created in Oracle Home location.
A folder called Oracle_IDM1 gets created and this is the IDM home.
Next step is to configure the Oracle Access Manager by creating WebLogic domain which will be covered in a seperate post.
Installing Oracle Database 11g R2 (11.2.0.1.0)
First time ever, I have installed an Oracle Database and have given few important screen shots in this post.
You can download the database 11.2.0.1.0 software here.





You can download the database 11.2.0.1.0 software here.





Tuesday, August 31, 2010
Oracle Access Manager integration with BPEL worklist
This is a new task that I accomplished recently with lots of ups and downs. The objective is to achieve Single Sign-on or authentication of BPEL worklist using Oracle Access Manager.
The various component versions are:
1. OAM 10.1.4.3
2. BPEL Process Manager 10.1.3.4
3. Oracle Single Sign-on 10.1.4.3
There are 2 ways to integrate OAM with BPEL.
1. Direct integration using Access SDK
2. Using Oracle Single Sign-on
I followed the second approach as our environment is AIX and Access SDK is not availble for AIX servers. However, I would suggest first approach as OSSO is not a strategic product for single sign-on from 11g onwards and no further development will be carried upon OSSO.
Integration Process:
I am writing the procedue for integration using second approach.
The integration is divided into 2 bits. OSSO integration with BPEL and OSSO integration with OAM.
I have posted here in detail about the BPEL-OSSO integration. OSSO integration with OAM is avaiable in oracle by example here.
The hiccups and troubleshooting tips I used in this integration process are written here 1, 2.
The various component versions are:
1. OAM 10.1.4.3
2. BPEL Process Manager 10.1.3.4
3. Oracle Single Sign-on 10.1.4.3
There are 2 ways to integrate OAM with BPEL.
1. Direct integration using Access SDK
2. Using Oracle Single Sign-on
I followed the second approach as our environment is AIX and Access SDK is not availble for AIX servers. However, I would suggest first approach as OSSO is not a strategic product for single sign-on from 11g onwards and no further development will be carried upon OSSO.
Integration Process:
I am writing the procedue for integration using second approach.
The integration is divided into 2 bits. OSSO integration with BPEL and OSSO integration with OAM.
I have posted here in detail about the BPEL-OSSO integration. OSSO integration with OAM is avaiable in oracle by example here.
The hiccups and troubleshooting tips I used in this integration process are written here 1, 2.
Labels:
BPEL,
Integrations,
OAM,
OSSO,
Troubleshooting Tips
Tuesday, August 3, 2010
OAM 11g is out
Much awaiting product Oracle Access Manager 11g is released along with few more products Oracle Adaptive Access Manager 11g, Oracle Identity Manager 11g on 20th July.
Software downloads of Oracle Identity and Access Management (11.1.1.3.0) , Oracle Access Manager WebGates (11.1.1.3.0) are available here.
Documentation for the same is available here.
Soon I will come up with more posts working on Oracle Access Manager 11g.
Software downloads of Oracle Identity and Access Management (11.1.1.3.0) , Oracle Access Manager WebGates (11.1.1.3.0) are available here.
Documentation for the same is available here.
Soon I will come up with more posts working on Oracle Access Manager 11g.
Monday, August 2, 2010
Is WebLogic Server needs to be integrated with Oracle Access Manager always?
I have had this question in my mind for a while that whether WebLogic Server needs to be integrated with Oracle Access Manager always?
Well, No! It depends on what task needs to be achieved. It is apparent that in order to protect a sample application deployed in WebLogic Server using Oracle Access Manager, we need to integrate using Identity Asserter (a common method). If the weblogic application is just reading some header variables passed by front end system (which can be Reverse Proxy) and if the WebLogic server can be configured with Provider that communicates to backend of Oracle Access Manager to fetch the user/group for role membership to set the user subject then Integration is not required.
My research results are:
You have very simple application (that just reads http header variables) deployed on WebLogic Server. A security provider (Authenticator) needs to be created in WebLogic realm to talk to OAM user directory (an LDAP). Employ a Reverse proxy in-line with WebLogic server with a WebGate on it. Assume you have protected the application using an authentication scheme in OAM.
When you access the application, Oracle Access Manager prompts for login details. After OAM authenticates and authorizes the user, the control reaches the WebLogic server where the principal will be set and the Authenticator fetches for group membership details to set the WebLogic user subject. This means that user authenticated by the OAM will be present (part of) in WebLogic Server.
Next research would be to test the sample application, but this time I am going to take the userid from container rather than taking it from header variable.
So keep tuned to this blog for more interesting topics!
Well, No! It depends on what task needs to be achieved. It is apparent that in order to protect a sample application deployed in WebLogic Server using Oracle Access Manager, we need to integrate using Identity Asserter (a common method). If the weblogic application is just reading some header variables passed by front end system (which can be Reverse Proxy) and if the WebLogic server can be configured with Provider that communicates to backend of Oracle Access Manager to fetch the user/group for role membership to set the user subject then Integration is not required.
My research results are:
You have very simple application (that just reads http header variables) deployed on WebLogic Server. A security provider (Authenticator) needs to be created in WebLogic realm to talk to OAM user directory (an LDAP). Employ a Reverse proxy in-line with WebLogic server with a WebGate on it. Assume you have protected the application using an authentication scheme in OAM.
When you access the application, Oracle Access Manager prompts for login details. After OAM authenticates and authorizes the user, the control reaches the WebLogic server where the principal will be set and the Authenticator fetches for group membership details to set the WebLogic user subject. This means that user authenticated by the OAM will be present (part of) in WebLogic Server.
Next research would be to test the sample application, but this time I am going to take the userid from container rather than taking it from header variable.
So keep tuned to this blog for more interesting topics!
Wednesday, June 9, 2010
How to protect applications deployed in Tomcat using Oracle Access Manager
Hi all,
Oracle Access Manager has webgates for many of the web servers provided out of the box. What if the application deployed on Tomcat has to be protected using Oracle Access Manager for authentication and authorization purposes ? The problem lies either to do customization or to have reverse proxy server infront of Tomcat.
I have detailed this here.
The stuff I did not talk in that post are the pros and cons of using the approach of Reverse Proxy fronting the Tomcat.
The prons of using Reverse proxy approach is that there is no need of customization or coding efforts required. All you need is just a webgate on RP server. All the future enhancements to the target application (which is deployed in Tomcat) does not effect / require changes in OAM side (may be minimal if not).
The cons of this approach is that there will be redirection for every request from RP to Tomcat server. So, the redirections will cause the time delay in real time.
Oracle Access Manager has webgates for many of the web servers provided out of the box. What if the application deployed on Tomcat has to be protected using Oracle Access Manager for authentication and authorization purposes ? The problem lies either to do customization or to have reverse proxy server infront of Tomcat.
I have detailed this here.
The stuff I did not talk in that post are the pros and cons of using the approach of Reverse Proxy fronting the Tomcat.
The prons of using Reverse proxy approach is that there is no need of customization or coding efforts required. All you need is just a webgate on RP server. All the future enhancements to the target application (which is deployed in Tomcat) does not effect / require changes in OAM side (may be minimal if not).
The cons of this approach is that there will be redirection for every request from RP to Tomcat server. So, the redirections will cause the time delay in real time.
Monday, June 7, 2010
Oracle Access Manager 10.1.4.3 integration with WebLogic Server.
Hi all,
If you are looking for WebLogic server integration with Oracle Access Manager 10.1.4.3, here it is..
Unfortunately, I could not continue to write posts in my blog, hence redirecting all the posts to the site http://onlineappsdba.com
Save the time!!
If you are looking for WebLogic server integration with Oracle Access Manager 10.1.4.3, here it is..
Unfortunately, I could not continue to write posts in my blog, hence redirecting all the posts to the site http://onlineappsdba.com
Save the time!!
Thursday, March 11, 2010
Fraudster managed to siphon off $4m in Wipro.
It is more of an internal users involved in fraud activities than outers and was witnessed in a high profile company, Wipro. Its time to wake up and ensure to tighten more security controls in Financial Departments after discovering the activities made by an employee.
check this
check this
Tuesday, March 9, 2010
5 Keys to a Successful Identity and Access Management Implementation
I have come across a white paper that talks about 5 ways to implement IDM solution successfully.
Here it is, http://viewer.bitpipe.com/viewer/viewDocument.do?accessId=11765255.
Here it is, http://viewer.bitpipe.com/viewer/viewDocument.do?accessId=11765255.
Thursday, February 25, 2010
Troubleshooting SSPI Integration
Hi all,
This time I would like to post the troubleshooting tips for issues that I have come across with the SSPI integration of Oracle Access Manager. I have given most probable solutions for the errors and it may differ based up on environment and approach followed. This is applicable for WebLogic servers till 10.3.0 and not for WebLogic 10.3.1 and higher.
1. Error:
Problem invoking WLST - Traceback (innermost last):
File “D:\wlsConnector\NetPointSecuProvForWeblogic\setupNetPointRealm_wl92.py”,
line 187, in ?
File “D:\wlsConnector\NetPointSecuProvForWeblogic\setupNetPointRealm_wl92.py”,
line 154, in create_AuthenticationProvider_14
java.lang.AssertionError: java.lang.reflect.UndeclaredThrowableException
at weblogic.descriptor.internal.AbstractDescriptorBean._createChildBean(
AbstractDescriptorBean.java:748)
at weblogic.management.security.RealmMBeanImpl.createAuthenticationProvi
der(RealmMBeanImpl.java:581)
Scenario: While running this setupNetPointRealm_wl92.cmd.
Solution: Weblogic Security Provider policy domain would be existing already in the OAM. So delete that policy domain and run the setupNetPointRealm_wl92.cmd again.
2. Error:
File “D:\oracle\OAM\wlsConnector\NetPointSecuProvForWeblogic\setupNetPointReal
m_wl92.py”, line 187, in ?
File “D:\oracle\OAM\wlsConnector\NetPointSecuProvForWeblogic\setupNetPointReal
m_wl92.py”, line 154, in create_AuthenticationProvider_14
java.lang.AssertionError: java.lang.NoClassDefFoundError: com/oblix/access/ObCon
fig
at weblogic.descriptor.internal.AbstractDescriptorBean._createChildBean(
AbstractDescriptorBean.java:748)
at weblogic.management.security.RealmMBeanImpl.createAuthenticationProvi
der(RealmMBeanImpl.java:581)
Scenario: While running setupNetPointRealm_wl92.cmd, it has thrown the error NoClassDefFoundError of com/oblix/access/ObConfig.
Solution: Check if the jars path is specified correctly in setDomainEnv.cmd and examine if there are misquotes (”) in the cmd file.
3. Error: Malformed \uxxxx encoding
Scenario: Running the runDeployerTool.cmd resulted with that error
Solution: While modifying changes to NetPointWeblogicTools.properties, open it in notepad instead of editplus and change the schemes.
Also, replace \ with /
4. Error:
D:\wlsConnector\NetPointSecuProvForWeblogic\oblix\tools\npWLTools>D:/bea/jdk160_05/bin/java com.oblix.weblogic.tools.NetPointPolicyDeployer orcladmin password
Using /D:/wlsConnector/NetPointSecuProvForWeblogic/oblix/tools/npWLTools/NetPoin
tWeblogicTools.properties
OB_InstallDir:D:/wlsConnector/NetPointSecuProvForWeblogic
Error 11004, oamhost.domain.com:6021Error 11004, oamhost.domain.com:6021Error 11004, oamhost.domain.com:6021Error 11004, oamhost.domain.com:6021
Access SDK ( AM API) initialize failed, please check log file for error messages
and re-run NetPointPolicyDeployer
Scenario: While running the tool runDeployerTool.cmd to create weblogic policy domain.
Solution: Check if you are able to ping oamhost.domain.com machine. It could be connectivity issue.
This time I would like to post the troubleshooting tips for issues that I have come across with the SSPI integration of Oracle Access Manager. I have given most probable solutions for the errors and it may differ based up on environment and approach followed. This is applicable for WebLogic servers till 10.3.0 and not for WebLogic 10.3.1 and higher.
1. Error:
Problem invoking WLST - Traceback (innermost last):
File “D:\wlsConnector\NetPointSecuProvForWeblogic\setupNetPointRealm_wl92.py”,
line 187, in ?
File “D:\wlsConnector\NetPointSecuProvForWeblogic\setupNetPointRealm_wl92.py”,
line 154, in create_AuthenticationProvider_14
java.lang.AssertionError: java.lang.reflect.UndeclaredThrowableException
at weblogic.descriptor.internal.AbstractDescriptorBean._createChildBean(
AbstractDescriptorBean.java:748)
at weblogic.management.security.RealmMBeanImpl.createAuthenticationProvi
der(RealmMBeanImpl.java:581)
Scenario: While running this setupNetPointRealm_wl92.cmd.
Solution: Weblogic Security Provider policy domain would be existing already in the OAM. So delete that policy domain and run the setupNetPointRealm_wl92.cmd again.
2. Error:
File “D:\oracle\OAM\wlsConnector\NetPointSecuProvForWeblogic\setupNetPointReal
m_wl92.py”, line 187, in ?
File “D:\oracle\OAM\wlsConnector\NetPointSecuProvForWeblogic\setupNetPointReal
m_wl92.py”, line 154, in create_AuthenticationProvider_14
java.lang.AssertionError: java.lang.NoClassDefFoundError: com/oblix/access/ObCon
fig
at weblogic.descriptor.internal.AbstractDescriptorBean._createChildBean(
AbstractDescriptorBean.java:748)
at weblogic.management.security.RealmMBeanImpl.createAuthenticationProvi
der(RealmMBeanImpl.java:581)
Scenario: While running setupNetPointRealm_wl92.cmd, it has thrown the error NoClassDefFoundError of com/oblix/access/ObConfig.
Solution: Check if the jars path is specified correctly in setDomainEnv.cmd and examine if there are misquotes (”) in the cmd file.
3. Error: Malformed \uxxxx encoding
Scenario: Running the runDeployerTool.cmd resulted with that error
Solution: While modifying changes to NetPointWeblogicTools.properties, open it in notepad instead of editplus and change the schemes.
Also, replace \ with /
4. Error:
D:\wlsConnector\NetPointSecuProvForWeblogic\oblix\tools\npWLTools>D:/bea/jdk160_05/bin/java com.oblix.weblogic.tools.NetPointPolicyDeployer orcladmin password
Using /D:/wlsConnector/NetPointSecuProvForWeblogic/oblix/tools/npWLTools/NetPoin
tWeblogicTools.properties
OB_InstallDir:D:/wlsConnector/NetPointSecuProvForWeblogic
Error 11004, oamhost.domain.com:6021Error 11004, oamhost.domain.com:6021Error 11004, oamhost.domain.com:6021Error 11004, oamhost.domain.com:6021
Access SDK ( AM API) initialize failed, please check log file for error messages
and re-run NetPointPolicyDeployer
Scenario: While running the tool runDeployerTool.cmd to create weblogic policy domain.
Solution: Check if you are able to ping oamhost.domain.com machine. It could be connectivity issue.
Labels:
OAM,
Troubleshooting Tips,
WebLogic
Configure Reverse Proxy for Oracle Access Manager consoles
Though it is not tough job to implement this, I thought there is nothing wrong in sharing. It is some times necessary to reverse proxy Oracle Access Manger consoles through Oracle HTTP Server or Apache Server etc.,
Lets assume the OAM consoles are like this:
http://oam.domain.com:7007/access/oblix
http://oam.domain.com:7007/identity/oblix
Lets assume you have OHS or Apache server running on port 80. Open the httpd.conf file and goto the end of the file and paste the below lines.
ProxyPass /access/oblix http://oam.domain.com:7007/access/oblix
ProxyPassReverse /access/oblix http://oam.domain.com:7007/access/oblix
ProxyPass /identity/oblix http://oam.domain.com:7007/identity/oblix
ProxyPassReverse /identity/oblix http://oam.domain.com:7007/identity/oblix
Now, you can access the OAM consoles through Apache server with the url, http://apache_host_name/access/oblix.
Lets assume the OAM consoles are like this:
http://oam.domain.com:7007/access/oblix
http://oam.domain.com:7007/identity/oblix
Lets assume you have OHS or Apache server running on port 80. Open the httpd.conf file and goto the end of the file and paste the below lines.
ProxyPass /access/oblix http://oam.domain.com:7007/access/oblix
ProxyPassReverse /access/oblix http://oam.domain.com:7007/access/oblix
ProxyPass /identity/oblix http://oam.domain.com:7007/identity/oblix
ProxyPassReverse /identity/oblix http://oam.domain.com:7007/identity/oblix
Now, you can access the OAM consoles through Apache server with the url, http://apache_host_name/access/oblix.
Wednesday, February 24, 2010
Integrating Oracle Access Manager with WebLogic Server 10g
Hi all,
This post will talk about the integration between Oracle Access Manager 10g with WebLogic Server 10g. This is not applicable for WebLogic versions 10.3.1 and higher. The functionality achieved with this integration is to get the Single Sign-On between applications deployed on WebLogic Server (webLogic resource) and non-WebLogic resources. Therefore SSPI connector can be used to achieve Single Sign-On between OAM access gates and web gates.
Infrastructure involved:
It is good to upgrade the Oracle Access Manager to 10.1.4.2 if you are using 10.1.4.1 as there are some bugs associated with this integration.
WebLogic SSPI can be downloaded here (linux) or here (windows). Here I have selected OHS as reverse proxy and this can be any other webserver of your choice provided WebGate is already there.
Until WebLogic Server 10.3.0, this integration has been achieved using SSPI connector.
Security Service Provider Interface (SSPI) Connector:
WebLogic security framework and WLS connector are based on J2EE standards and an implementation of JAAS. Together, WebLogic implementation of JAAS is called SSPI. SSPI consists of several provider modules such as Authentication provider, Identity Asserter, Authorization provider, Role Mapping provider, Deployment Provider.
Authentication Provider: This provider uses OAM authentication services to authenticate users (based on username and password) who acces WebLogic applications. This provider does not provide Single Sign-On capability.
Authorization Provider: This provider uses OAM authorization services to authenticate users who access WebLogic resource. The authorization is done based on policies that are specified in the Policy Manager.
Identity Asserter: This is very essential provider when a user wants Single Sign-On capability. This is similar to Authentication provider which validates the already authenticated user based on ObSSOCookie. This is used in case of proxied configuration.
Role Mapper: This provider returns security roles of a user. The groups that the user is part of, are returned as part of actions configured in a authentication policy of policy domain.
Deployment Provider: This provider (though not part of JAAS specification) monitors the applications that are deployed or undeployed on the WebLogic Server and writes information about these applications to either
Architecture:


Process Flow:
Installation and Configuration:
This integration involves:
SSPI connector communicates with both Identity and Access Servers. SSPI connector also expects user information about privileges, groups, actions, responses etc., you will need an user with respect to SSPI to talk to access server. Lets name the user as wlsadmin (create the user) and assign the user Master Identity Administrator, Master Administrator, Delegated Identity Administrator.
1. Create the resource type definitions in OAM for the following.
Name: Oracle WebLogic Access and Identity authentication scheme
Description: Used to authenticate users who access WebLogic resources.
Level: 1
Challenge Method: Basic
Challenge Parameter: realm:Oracle Access and Identity
SSL Required: No
Challenge Redirect: (Leave blank)
Enabled: (Leave as is)
Specify the credential_mapping and validate_password plugin values as shown below.
3. Create the second authentication scheme for un-protecting certain resources, such as gif images in WebLogic resources using the following details and the Anonymous authentication scheme as a template:
General tab:
Name: Oracle WebLogic Anonymous Authentication
Description: Used to un-protect gifs, and so on.
Level: 0
Challenge Method: Anonymous
Parameter: (Leave blank)
SSL Required: No
Challenge Redirect: (Leave blank)
Enabled: Yes
Provide the plugin values as shown below.
5. Backup the config.xml and boot.properties.
6. Install the SSPI connector. The steps are straight forward and I will make a note of few things to remember.
Select Advanced as Configuration option.
Enter allow for Map the authorization result obstain.
Enter the webpass hostname and port.
Enter the user and group search attributes.
Select the transport mode option as open or simple or cert.
Enter the access gate details as specified in Access gate profile.
Configure SSPI connector:
1. Goto the location sspi_install_dir/
2. Take backup of files
3. Edit the file
Note:Be careful with WLC_LIB_CLASSPATH value as it should not have any spaces or line breaks.
7. Comment the existing classpath and replace with a new one as shown below.
CLASSPATH=”${PRE_CLASSPATH}${CLASSPATHSEP}${WLC_LIB_CLASSPATH}${CLASSPATHSEP}${WEBLOGIC_CLASSPATH}${CLASSPATHSEP}${POST_CLASSPATH}$
{CLASSPATHSEP}${WLP_POST_CLASSPATH}”
export CLASSPATH
8. Restart the weblogic server. Now you should see the new jars in the classpath.
9. Take a backup of file
10. Edit the file
Enter the hostname, domain name, weblogic server port, username and password details and save it.
11. Goto the location sspi_connector/NetPointSecuProvForWeblogic and execute setupNetPointRealm_wl92.sh.
Note: Though you are using weblogic server 10.3.0, you should execute setupNetPointRealm_wl92.sh file, don’t execute the file setupNetPointRealm.sh.
12. This script will create the NetPointRealm with necessary security providers.
Deploy Policy Domains:
1. Take backup of file
2. Create a file runDeployerTool.sh under this location
export CLASSPATHSEP=”:”
export OAMWLC=”sspi_conn/NetPointSecuProvForWeblogic”
export OAMWLCDIR=”${OAMWLC}/oblix”
export CLASSPATH=”${CLASSPATH}${CLASSPATHSEP}${OAMWLCDIR}/lib/jobaccess.jar${CLASSPATHSEP}${OAMWLCDIR}/tools/npWLTools;
${CLASSPATHSEP}${OAMWLCDIR}/tools/npWLTools/npWLTools.jar”
export PATH=”${PATH}:${OAMWLCDIR}/lib”
export LD_LIBRARY_PATH=”${OAMWLCDIR}/lib”
echo $CLASSPATH
/u01/jdk160_05/bin/java com.oblix.weblogic.tools.NetPointPolicyDeployer wlsadmin password
Note: This is for linux environment, if its windows, follow the one shown below.
set CLASSPATHSEP=;
set OAMWLC=D:/sspi_Connector/NetPointSecuProvForWeblogic
set OAMWLCDIR=%OAMWLC%/oblix
set CLASSPATH=%CLASSPATH%;%OAMWLCDIR%/lib/jobaccess.jar;%OAMWLCDIR%/tools/npWLTools;%OAMWLCDIR%/tools/npWLTools/npWLTools.jar
set PATH=%PATH%;%OAMWLCDIR%/lib
set LD_LIBRARY_PATH=%OAMWLCDIR%/lib
echo %CLASSPATH%
D:/bea/jdk160_05/bin/java com.oblix.weblogic.tools.NetPointPolicyDeployer wlsadmin password
3. Run the deployertool and check the log for any errors. This tool will create a policy domain with resources, authorization policies etc., and verify it by logging it to OAM policy manager console.
4. Now login to weblogic console and inspect the new realm NetPointRealm created. Check for users and groups, security providers etc., Remember that this is not default realm yet.
5. Goto the providers tab, Certification Path and click the WebLogicCertPathProvivider and enable the check box set current builder.
6. Enable NetPointRealm as default realm in the console.
7. Stop the WebLogic server. Change the boot.properties file and edit the username and password with wlsadmin and password values.
8. Start the weblogic server and you should see Netpointrealm is the default realm and you should be able to login to WLS console using wlsadmin and password.
Deploy the WebLogic application:
You can deploy a sample weblogic application to the server where Netpointrealm is the default realm. Goto the WebLogic policy domain in OAM console and add the resource /sample/index.jsp and save it.
Configure Reverse Proxy:
1. In this case, I have used OHS as reverse proxy.
2. Create a OHS webgate profile in OAM console and install the OHS webgate. I am not briefing about this more as its pretty straight forward.
3. Edit the httpd.conf file of OHS server and goto the end of file and enter the following lines.
ProxyPass /sample http://sspi_hostname:port/sample
Test the SSO:
1. Now access the application http://reverseproxy_hostname:port/sample.
2. You will be challenged with credentials with the authentication scheme configured for it.
3. If you access any other resource protected by the OAM with the same authentication level configured for /sample application, you should be able to access it directly without re-authentication.
Troubleshooting Tips:
Refer the Oracle Documentation.
References:
Oracle SSPI Integration guide
This post will talk about the integration between Oracle Access Manager 10g with WebLogic Server 10g. This is not applicable for WebLogic versions 10.3.1 and higher. The functionality achieved with this integration is to get the Single Sign-On between applications deployed on WebLogic Server (webLogic resource) and non-WebLogic resources. Therefore SSPI connector can be used to achieve Single Sign-On between OAM access gates and web gates.
Infrastructure involved:
- Oracle Access Manager 10.1.4.2 and higher
- WebLogic SSPI
- Oracle HTTP Server (for reverse proxy)
It is good to upgrade the Oracle Access Manager to 10.1.4.2 if you are using 10.1.4.1 as there are some bugs associated with this integration.
WebLogic SSPI can be downloaded here (linux) or here (windows). Here I have selected OHS as reverse proxy and this can be any other webserver of your choice provided WebGate is already there.
Until WebLogic Server 10.3.0, this integration has been achieved using SSPI connector.
Security Service Provider Interface (SSPI) Connector:
WebLogic security framework and WLS connector are based on J2EE standards and an implementation of JAAS. Together, WebLogic implementation of JAAS is called SSPI. SSPI consists of several provider modules such as Authentication provider, Identity Asserter, Authorization provider, Role Mapping provider, Deployment Provider.
Authentication Provider: This provider uses OAM authentication services to authenticate users (based on username and password) who acces WebLogic applications. This provider does not provide Single Sign-On capability.
Authorization Provider: This provider uses OAM authorization services to authenticate users who access WebLogic resource. The authorization is done based on policies that are specified in the Policy Manager.
Identity Asserter: This is very essential provider when a user wants Single Sign-On capability. This is similar to Authentication provider which validates the already authenticated user based on ObSSOCookie. This is used in case of proxied configuration.
Role Mapper: This provider returns security roles of a user. The groups that the user is part of, are returned as part of actions configured in a authentication policy of policy domain.
Deployment Provider: This provider (though not part of JAAS specification) monitors the applications that are deployed or undeployed on the WebLogic Server and writes information about these applications to either
NetPointDeployPolicy.txt or NetPointUndeployPolicy.txt. Architecture:
Process Flow:
- User requests for a WebLogic resource protected by OAM. In this case, the authen method configured in web.xml should be CLIENT-CERT.
- WebGate intercepts the request and checks wit the Access Server whether the resource is protected or not. If the resource is protected, it fetches the Authentication scheme configured for that resource.
- User is challenged for username and password based on the Auth scheme configured for that resource.
- User submits the credentials.
- WebGate will pass the credentials to Access Server for validation. If the user is authenticated successfully, access server creates session token and passes to WebGate. Webgate will set the ObSSOCookie and appends it in HTTP Header. The plugin configured in the Proxy server (mod_proxy) will forward the request to the WebLogic server.
- The WebLogic server plugin passes the cookie to WebLogic server.
- WebLogic security framework invokes the SSPI connector which inturn invokes the Identity Asserter. The Identity Asserter expects ObSSOCookie as an external token for validating the user. The Asserter sets the cookie in the HTTP response object once it validates the token.
- The Identity Asserter extracts the cookie from HTTP header. The Asserter retrieves the user identity from the Access Server using a return action defined in a special auth scheme in OAM. A resource with URL /Authen/Basic is protected by OAM and is used by SSPI internally to authenticate users.
- The Authorization provider talks to the Access Server to verify whether the user is authorized to access the resource or not. The Role Mapping provider uses the access gate to communicate with the Access Server to determine what OAM roles are defined to the user. These roles are mapped to security roles in WebLogic. In OAM, these roles are defined as return action /Authen/Roles when getting an authorization policy.
Installation and Configuration:
This integration involves:
- Configure OAM for SSPI
- SSPI connector install
- Configure SSPI Connector
- Deploy Policy Domains
- Deploy WebLogic Application
- Configure Reverse proxy
- Test for SSO
- Troubleshooting
SSPI connector communicates with both Identity and Access Servers. SSPI connector also expects user information about privileges, groups, actions, responses etc., you will need an user with respect to SSPI to talk to access server. Lets name the user as wlsadmin (create the user) and assign the user Master Identity Administrator, Master Administrator, Delegated Identity Administrator.
1. Create the resource type definitions in OAM for the following.
wl_url: resource operation as GET and POSTwl_svr: resource operation as BOOT and DEFAULTwl_adm:resource operation as DEFAULTwl_ejb:resource operation asEXECUTEwl_authen:resource operation asLOGIN
Name: Oracle WebLogic Access and Identity authentication scheme
Description: Used to authenticate users who access WebLogic resources.
Level: 1
Challenge Method: Basic
Challenge Parameter: realm:Oracle Access and Identity
SSL Required: No
Challenge Redirect: (Leave blank)
Enabled: (Leave as is)
Specify the credential_mapping and validate_password plugin values as shown below.
credential_mapping obMappingBase="o=company,c=us",obMappingFilter= "(&(&(objectclass=inetorgperson)(uid=%userid%)) (|(!(obuseraccountcontrol=*)) (obuseraccountcontrol=ACTIVATED)))"
validate_password obCredentialPassword="password"Specify the domain name (o=company,c=us) as per your environment.
3. Create the second authentication scheme for un-protecting certain resources, such as gif images in WebLogic resources using the following details and the Anonymous authentication scheme as a template:
General tab:
Name: Oracle WebLogic Anonymous Authentication
Description: Used to un-protect gifs, and so on.
Level: 0
Challenge Method: Anonymous
Parameter: (Leave blank)
SSL Required: No
Challenge Redirect: (Leave blank)
Enabled: Yes
Provide the plugin values as shown below.
credential_mapping obMappingBase="o=company,c=us",obMappingFilter="
(uid=OblixAnonymous)"4. Configure an Access Gate for SSPI connector. This is the access gate used by security providers to communicate with Access Server. Follow the OAM installation guide for creating an access gate. FYI, port need not be specified.5. Backup the config.xml and boot.properties.
6. Install the SSPI connector. The steps are straight forward and I will make a note of few things to remember.
Select Advanced as Configuration option.
Enter allow for Map the authorization result obstain.
Enter the webpass hostname and port.
Enter the user and group search attributes.
Select the transport mode option as open or simple or cert.
Enter the access gate details as specified in Access gate profile.
Configure SSPI connector:
1. Goto the location sspi_install_dir/
NetPointSecuProvForWeblogic.2. Take backup of files
NetPointResourceMap.conf, NetPointResourceMap.conf and NetPointProvidersConfig.properties.3. Edit the file
NetPointProvidersConfig.properties with following valuesOB_LogLevel=InfoOB_LogLevel=sspi_conn_install/NetPointSecuProvForWeblogic/OB_AdminUserName=wlsadminOB_AdminUserCreds=passwordOB_CookieDomain=.domain.com (change it as per your environment)4. Copy the file
NetPointResourceMap.conf and NetPointProvidersConfig.properties to weblogic domain directory.5. Copy the
wl92NetPointSecurityProviders.jar from sspi_conn/NetPointSecuProvForWeblogic/oblix/lib/mbeantypes/wl92NetPointSecurityProviders.jar to wlsserver_103/server/lib/mbeantypes.6. Take a backup of file setDomainEnv.sh or cmd and edit the file with values as shown below.
Search for end of file and place this text after export JAVA_OPTIONS line.
# SET WLSConnector Classpath and other paths
export OAMWLC="/u01/oracle/sspi/NetPointSecuProvForWeblogic"
export OAMWLCDIR="${OAMWLC}/oblix/lib"
LD_LIBRARY_PATH="${OAMWLCDIR}"
export LD_LIBRARY_PATH
export PATH="${PATH}:${OAMWLCDIR}"
export WLC_LIB_CLASSPATH="${OAMWLCDIR}/jobaccess.jar${CLASSPATHSEP}${OAMWLCDIR}/bcprov-jdk14-125.jar${CLASSPATHSEP}
${OAMWLCDIR}/wlNetPoint.jar${CLASSPATHSEP}${OAMWLCDIR}/xerces.jar"7. Comment the existing classpath and replace with a new one as shown below.
CLASSPATH=”${PRE_CLASSPATH}${CLASSPATHSEP}${WLC_LIB_CLASSPATH}${CLASSPATHSEP}${WEBLOGIC_CLASSPATH}${CLASSPATHSEP}${POST_CLASSPATH}$
{CLASSPATHSEP}${WLP_POST_CLASSPATH}”
export CLASSPATH
8. Restart the weblogic server. Now you should see the new jars in the classpath.
9. Take a backup of file
setupNetPointRealm.properties present in the location sspi_connector/NetPointSecuProvForWeblogic.10. Edit the file
setupNetPointRealm.properties with values as shown below.Enter the hostname, domain name, weblogic server port, username and password details and save it.
11. Goto the location sspi_connector/NetPointSecuProvForWeblogic and execute setupNetPointRealm_wl92.sh.
Note: Though you are using weblogic server 10.3.0, you should execute setupNetPointRealm_wl92.sh file, don’t execute the file setupNetPointRealm.sh.
12. This script will create the NetPointRealm with necessary security providers.
Deploy Policy Domains:
1. Take backup of file
NetPointWeblogicTools.properties present in location sspi_conn/NetPointSecuProvForWeblogic/oblix/tools/npWLTools and edit with values as given below.ObWLTools.Debug=trueObPolicyDomain.Name=WebLogic Server Security ProviderObWLTools.DeployPolicy=falseObWLSDomain.Dir=weblogic directory location ObWLAuthenticationScheme.Name=OAM WebLogic Server Basic AuthenticationObWLNoneAuthenticationScheme.Name=OAM WebLogic Anonymous Authentication2. Create a file runDeployerTool.sh under this location
sspi_conn/NetPointSecuProvForWeblogic/oblix/tools/npWLToolsexport CLASSPATHSEP=”:”
export OAMWLC=”sspi_conn/NetPointSecuProvForWeblogic”
export OAMWLCDIR=”${OAMWLC}/oblix”
export CLASSPATH=”${CLASSPATH}${CLASSPATHSEP}${OAMWLCDIR}/lib/jobaccess.jar${CLASSPATHSEP}${OAMWLCDIR}/tools/npWLTools;
${CLASSPATHSEP}${OAMWLCDIR}/tools/npWLTools/npWLTools.jar”
export PATH=”${PATH}:${OAMWLCDIR}/lib”
export LD_LIBRARY_PATH=”${OAMWLCDIR}/lib”
echo $CLASSPATH
/u01/jdk160_05/bin/java com.oblix.weblogic.tools.NetPointPolicyDeployer wlsadmin password
Note: This is for linux environment, if its windows, follow the one shown below.
set CLASSPATHSEP=;
set OAMWLC=D:/sspi_Connector/NetPointSecuProvForWeblogic
set OAMWLCDIR=%OAMWLC%/oblix
set CLASSPATH=%CLASSPATH%;%OAMWLCDIR%/lib/jobaccess.jar;%OAMWLCDIR%/tools/npWLTools;%OAMWLCDIR%/tools/npWLTools/npWLTools.jar
set PATH=%PATH%;%OAMWLCDIR%/lib
set LD_LIBRARY_PATH=%OAMWLCDIR%/lib
echo %CLASSPATH%
D:/bea/jdk160_05/bin/java com.oblix.weblogic.tools.NetPointPolicyDeployer wlsadmin password
3. Run the deployertool and check the log for any errors. This tool will create a policy domain with resources, authorization policies etc., and verify it by logging it to OAM policy manager console.
4. Now login to weblogic console and inspect the new realm NetPointRealm created. Check for users and groups, security providers etc., Remember that this is not default realm yet.
5. Goto the providers tab, Certification Path and click the WebLogicCertPathProvivider and enable the check box set current builder.
6. Enable NetPointRealm as default realm in the console.
7. Stop the WebLogic server. Change the boot.properties file and edit the username and password with wlsadmin and password values.
8. Start the weblogic server and you should see Netpointrealm is the default realm and you should be able to login to WLS console using wlsadmin and password.
Deploy the WebLogic application:
You can deploy a sample weblogic application to the server where Netpointrealm is the default realm. Goto the WebLogic policy domain in OAM console and add the resource /sample/index.jsp and save it.
Configure Reverse Proxy:
1. In this case, I have used OHS as reverse proxy.
2. Create a OHS webgate profile in OAM console and install the OHS webgate. I am not briefing about this more as its pretty straight forward.
3. Edit the httpd.conf file of OHS server and goto the end of file and enter the following lines.
ProxyPass /sample http://sspi_hostname:port/sample
Test the SSO:
1. Now access the application http://reverseproxy_hostname:port/sample.
2. You will be challenged with credentials with the authentication scheme configured for it.
3. If you access any other resource protected by the OAM with the same authentication level configured for /sample application, you should be able to access it directly without re-authentication.
Troubleshooting Tips:
Refer the Oracle Documentation.
References:
Oracle SSPI Integration guide
Labels:
Installations,
Integrations,
OAM,
WebLogic
Tuesday, February 23, 2010
Oracle Access Manager cache flush issue
I have come across an issue with Oracle Access Manager and Identity XML and thought its worth sharing. The scenario is that, when you try to modify an user attribute using Identity XML and if you access any resource where the authorization is provided based on that specific attribute value, then it returns an error “Oracle Access Manager Operation Error”.
This means that the attribute updated in identity system (with backend as LDAP) using Identity XML has not been communicated to the Access Server. So when the resource is accessed where the atz is given based on the attribute, the authorization will fail and hence will result with that error. If you have specified an Authorization failure URL, then user will be taken to that URL.
The solution for this issue is to flush the access server as and when the changes happen to the identity system and there should be automatic cache flush between identity and access system.
This is done by changing the parameter value of doAccessServerFlush from ‘false’ to ‘true’ in baseddbparams.xm. This file is located in the directory Identity_server_installation_directory/oblix/data/common.
Also, the cache timeout param values present in the webgates and access gates has to be reduced (for instance, reduce from 1800 to 100), this has to be followed by Identity and Access servers restart.
Refer the Oracle Documentation for this .
This means that the attribute updated in identity system (with backend as LDAP) using Identity XML has not been communicated to the Access Server. So when the resource is accessed where the atz is given based on the attribute, the authorization will fail and hence will result with that error. If you have specified an Authorization failure URL, then user will be taken to that URL.
The solution for this issue is to flush the access server as and when the changes happen to the identity system and there should be automatic cache flush between identity and access system.
This is done by changing the parameter value of doAccessServerFlush from ‘false’ to ‘true’ in baseddbparams.xm. This file is located in the directory Identity_server_installation_directory/oblix/data/common.
Also, the cache timeout param values present in the webgates and access gates has to be reduced (for instance, reduce from 1800 to 100), this has to be followed by Identity and Access servers restart.
Refer the Oracle Documentation for this .
Thursday, February 18, 2010
Protecting WebLogic Server application using Oracle Entitlement Server
This post talks about protecting a WebLogic server application using Oracle Entitlement Server. This means coarse grained access which is page level access based on user user roles. Though OES is meant for fine grained access, we will discuss how a basic WL app can be protected at first. Later if you want to provide ATN using OAM and ATZ using OES, you can follow this.
I will talk about installing a WebLogic SSM, configuring the SSM and protecting sample WL app using SSM.
Install WebLogic SSM: WL SSM is used only to protect weblogic apps.
Run the installer and provide the following details.
Applying Patch:The latest SSM patch available is CP3.
Extract the patch file and copy the patches folder to the $BEA_HOME/ales32-ssm
Edit the ApplySsmPatch.sh and provide jdk and ssm directory locations.
Run the patch as shown below.
To check status: ./ApplySsmPatch.sh status
To upgrade SSM to CP3
We will proceed to next step assuming the WebLogic domain is already created.
Configure SSM: This step involves creating an WL SSM instance
Edit the file myssm_config.properties for the following params.
wls.domain.dir = weblogic_domain_directory
ssm.conf.id = wlsapp (you will see )
db.password = abcd1234 (oes database user password used while running DBConfigTool)
ales.admin.password = abcd1234 (OES admin password)
ssm.admin.name = weblogic (Weblogic domain username)
ssm.admin.password = abcd1234
arme.port = 8000
ales.organization.scope = wlsapp_org (since CP3, Application scope is replaced with Organizational scope )
ales.identity.dir =wlsapp_dir (identity directory where users for this application in OES are stored)
db.jdbc.url = jdbc:oracle:thin:@db_server:1521:db_sid
db.jdbc.driver = oracle.jdbc.driver.OracleDriver (uncomment this line)
scm.name = adminconfig
Run the ConfigTool as shown below.
To check everything works: ./ConfigTool.sh -check myssm_config.properties (Advisory to run this command as it checks if there are any conflicts). The WebLogic server should be stopped before running this command.
To process : ./ConfigTool.sh -process myssm_config.properties
This will create the the WL SSM instance, organization with wlsapp in OES and policies.
Open the OES EUI console and access the Resources. Traverse to the organization wlsapp->shared->server and create New AdminServer and map it as Resource. Distribute the policies. Policy distributed is crucial and missing this will not allow weblogic server to start (will throw Authentication failed at booting stage) .
Start the WebLogic server.
Access the WLS console and see the new realm created and marked as true (default realm). Check the providers, Database Authenticator where the OES will authenticate users against the DB using this Authenticator.
I will talk about installing a WebLogic SSM, configuring the SSM and protecting sample WL app using SSM.
Install WebLogic SSM: WL SSM is used only to protect weblogic apps.
Run the installer and provide the following details.
- Select BEA Home (You can install SSM either in the same Admin home or in a different location)
- Select only OES SM For WLS [Notice OES SM Common is also selected ]
- Enter the SCM name if you want to associate the WL SSM to an SCM (optional)
- Enter the administration url eg., https://admin_host_name:port/
- Select the JDK (select latest version available in WebLogic server installation)
Applying Patch:The latest SSM patch available is CP3.
Extract the patch file and copy the patches folder to the $BEA_HOME/ales32-ssm
Edit the ApplySsmPatch.sh and provide jdk and ssm directory locations.
Run the patch as shown below.
To check status: ./ApplySsmPatch.sh status
To upgrade SSM to CP3
We will proceed to next step assuming the WebLogic domain is already created.
Configure SSM: This step involves creating an WL SSM instance
Edit the file myssm_config.properties for the following params.
wls.domain.dir = weblogic_domain_directory
ssm.conf.id = wlsapp (you will see )
db.password = abcd1234 (oes database user password used while running DBConfigTool)
ales.admin.password = abcd1234 (OES admin password)
ssm.admin.name = weblogic (Weblogic domain username)
ssm.admin.password = abcd1234
arme.port = 8000
ales.organization.scope = wlsapp_org (since CP3, Application scope is replaced with Organizational scope )
ales.identity.dir =wlsapp_dir (identity directory where users for this application in OES are stored)
db.jdbc.url = jdbc:oracle:thin:@db_server:1521:db_sid
db.jdbc.driver = oracle.jdbc.driver.OracleDriver (uncomment this line)
scm.name = adminconfig
Run the ConfigTool as shown below.
To check everything works: ./ConfigTool.sh -check myssm_config.properties (Advisory to run this command as it checks if there are any conflicts). The WebLogic server should be stopped before running this command.
To process : ./ConfigTool.sh -process myssm_config.properties
This will create the the WL SSM instance, organization with wlsapp in OES and policies.
Open the OES EUI console and access the Resources. Traverse to the organization wlsapp->shared->server and create New AdminServer and map it as Resource. Distribute the policies. Policy distributed is crucial and missing this will not allow weblogic server to start (will throw Authentication failed at booting stage) .
Start the WebLogic server.
Access the WLS console and see the new realm created and marked as true (default realm). Check the providers, Database Authenticator where the OES will authenticate users against the DB using this Authenticator.
Troubleshooting WebLogic Server
This post will present troubleshooting tips for errors that will across in WebLogic server.
Error: Problem invoking WLST - java.lang.UnsupportedClassVersionError: Bad version number in .class file
Done
Scenario: Trying to stop WebLogic Server
Solution: The jdk version used while creating the domain is not supported. Use higher version ( present in the same WebLogic server installed location) and point it while domain creation.
Note: I will be updating this post every now and then.
Error: Problem invoking WLST - java.lang.UnsupportedClassVersionError: Bad version number in .class file
Done
Scenario: Trying to stop WebLogic Server
Solution: The jdk version used while creating the domain is not supported. Use higher version ( present in the same WebLogic server installed location) and point it while domain creation.
Note: I will be updating this post every now and then.
Monday, February 1, 2010
Troubleshooting tips for LDAP command line tools
This post will talk about the problems and solutions that arises when LDAP command line tools are run for various scenarios.
Error:unable to locate message file: ldap.msb
Scenario: When you run any ldap tools like ldapmodify, ldapadd, ldapbind etc.,
Solution: Set the ORACLE_HOME env variable as shown below.
server@hostname homedir$ export ORACLE_HOME=/u01/orasoft/Oracle/Middleware/idm/Oracle_IDM1
server@hostname homedir$ echo $ORACLE_HOME
/u01/orasoft/Oracle/Middleware/idm/Oracle_IDM1
Now execute the ldap commands as shown below.
server@hostname homedir$ /u01/orasoft/Oracle/Middleware/idm/Oracle_IDM1/bin/ldapbind -h hostname -p 389 -D cn=orcladmin -w password
bind successful
Error:unable to locate message file: ldap
Scenario: When you run any ldap tools like ldapmodify, ldapadd, ldapbind etc.,
Solution: Set the ORACLE_HOME env variable as shown below.
server@hostname homedir$ export ORACLE_HOME=/u01/orasoft/Oracle/Middleware/idm/Oracle_IDM1
server@hostname homedir$ echo $ORACLE_HOME
/u01/orasoft/Oracle/Middleware/idm/Oracle_IDM1
Now execute the ldap commands as shown below.
server@hostname homedir$ /u01/orasoft/Oracle/Middleware/idm/Oracle_IDM1/bin/ldapbind -h hostname -p 389 -D cn=orcladmin -w password
bind successful
Wednesday, January 27, 2010
Oracle Identity & Access Management Questions & Answers
Identity and Access Management:
Q: What is an identity?
A: An identity is a piece of information used to identify an entity whether it is a user or group etc.,.
LDAP:
Q: What is an object class and their different types?
A: An object class specifies set of attributes that are used to define an object.
A:
dn: cn=subschemasubentry
changetype: modify
add: objectclasses
objectclasses: ( 1.2.3.4.5 NAME 'myOC'
DESC 'my Objectclass definition' MAY myAttr )
dn: cn=subschemasubentry
changetype: modify
add: attributetypes
attributetypes: ( 1.2.3.4.5.6.7 NAME "myAttr" DESC "New attribute definition" EQUALITY caseIgnoreMatch
SYNTAX "1.3.6.1.4.1.1466.115.121.1.15" )
dn: cn=person one,dc=example,dc=com
changetype: modify
add: myAttr
myAttr: myattrValue1
dn: cn=person one,dc=example,dc=com
changetype: modify
add: objectclass
objectclass: myOC
Adding an Auxiliary object class to a schema:
changetype: modify
add: objectclasses
objectclasses:inetorgperson
objectclasses: myAuxOC
Q: What is DN and RDN?
A: A DN is the LDAP entry that uniquely identifies and describes the entry in LDAP server.
cn=Jones,dc=oracle,dc=com is the DN of user Jones and RDN is cn=Jones.
Q: How do you define Identity Management & Access Management?
A: Identity Management enables customers to manage end-to-end lifecycle of user identities across all enterprise resources securely. Access Management provides web access management including authentication, fine grained authorization, federation and proactive online fraud prevention.
Q:What are various domains that fall under identity management?
A: Identity Management, Access Management, Directory Management. Oracle Products that fall under Identity Management are Oracle Identity Manager and Oracle Role Manager. Oracle products that fall under Access Management are Oracle Access Manager, Oracle Entitlement Server, Oracle Adaptive Access Manager, Oracle Identity federation and Enterprise Single Sign-On. Oracle products that fall under Directory Management are OID and OVD.
Oracle Access Manager:
Oracle Access Manager is a state-of-the-art solution for both centralized identity management and access control, providing an integrated standards-based solution that delivers authentication, web single sign-on, access policy creation and enforcement, user self-registration and self-service, delegated administration, reporting, and auditing.
Q: What is Single Sign On?
A: Single Sign-On allows users to sign on once to a protected application and gain access to the other protected resources within the same domain defined with same authentication level.
Q: What is multi domain Single Sign-On?
A: Multi Domain SSO gives users the ability to access more than one protected resource (URL and Applications), which are scattered across multiple domains with one time authentication.
Q: What is the authentication mechanism used by Oracle Access Manager?
A: ObSSOCookie and it is stateless.
Q: Explain various security modes present in Oracle Access Manager?
A:
Open: Allows unencrypted communication. In Open mode, there is no authentication or encryption between the AccessGate and Access Server. The AccessGate does not ask for proof of the Access Server's identity and the Access Server accepts connections from all AccessGates. Similarly, Identity Server does not require proof of identity from WebPass.
Simple: Supports encryption by Oracle. In Simple mode communications between Web clients (WebPass and Identity Server, Policy Manager and WebPass, and Access Server and WebGate are encrypted using TLS v1. In both Simple and Cert mode, Oracle Access Manager components use X.509 digital certificates only. This includes Cert Authentication between WebGates and the Access Server where the standard cert-decode plug-in decodes the certificate and passes certificate information to the standard credential_mapping authentication plug-in. For each public key there exists a corresponding private key that Oracle Access Manager stores in the aaa_key.pem file for the Access Server (or ois_key.pem for Identity Server).
Cert: Requires a third-party certificate. Use Cert (SSL) mode if you have an internal Certificate Authority (CA) for processing server certificates. In Cert mode, communication between WebGate and Access Server, and Identity Server and WebPass are encrypted using Transport Layer Security, RFC 2246 (TLS v1).
Q: Explain the architecture of Oracle Access Manager?
A: Oracle Access Manager architecture mainly consists for components such as Identity Server, WebPass, Policy Manager, Access Server and a WebGate. Identity Server is a standalone C++ server which communicates directly with LDAP.
It also receives requests and sends response to Webpass. WebPass is a web server plugin that passes info between identity server and webserver. It redirects HTTP requests from browser to Access Server, and sends Identity XML SOAP requests to Identity Server.
Policy Manager (PMP or PAP) is a web server plugin that communicates directly with user, configuration and policy repositories. Access Server is a stand alone C++ server and is also called PDP. It receives requests from & sends responses to WebGates/AccessGates.
It also communicates with LDAP. It answers Access Server SDK requests. WebGate (PEP) is a web server plugin that passes info between webserver and access server. It passes user authentication data to access server for processing.
Q: What are the ObSSOCookie Contents?
A: Cookie contains encrypted session token and non-encrypted data.
This Encrypted Session Token consists of : DN of the authenticated user, level of auth scheme, ip address of client to which cookie was issued, time the cookie is issued, time the cookie was last updated. If the user is not idle, then cookie will get automatically updated at a fixed interval to prevent session timeout. The updated interval is the 1/4 th of idle session timeout of accessgate.
The Unencrypted ObSSOCookie data contains cookie expiry time, domain in which cookie is valid, additional flag that determines if cookie can only be sent using SSL.
Q: What is the key used for encrypting the ObSSOCookie?
A: Shared Secret key. It is configured in the Identity Admin console and can be generated by the OAM administrator.
Q: What happens if the ObSSOCookie is tampered?
A: When access system generates ObSSOCookie, MD-5 hash is taken from session token. So when the user is authenticated again using the cookie, the MD5 hash is compared with original cookie contents. MD-5 hash is a one-way hash, hence it cant be unencrypted. Access server compares the cookie contents with hash. If both are not same, then cookie is tampered in the interim. This cookie does not contain username and password.
Q: What is the difference between WebGate and AccessGate?
A: WebGate is an out-of-the-box plug-in that intercepts Web resource (HTTP) requests and forwards them to the Access Server for authentication and authorization. An AccessGate is a custom webgate that can intercept requests of HTTP and non-HTTP resources.
Q: What are the major parameters defined in an authentication scheme?
A: The authentication scheme level which defines the level of the security defined for an application.
Q: Explain the flow when a user requests for an application protected by Oracle Access Manager?
A: The following steps describes the flow when a user makes a request to access a resource protected by the Oracle Access Manager.
A: Multi Domain SSO gives users the ability to access more than one protected resource (URL and Applications), which are scattered across multiple domains with one time authentication.
Lets assume that OAM components are installed in host1.domain1.com and we will designate host1.domain1.com as the primary authentication server.
* Host2.domain2.com with web gate (ex: webgate2) installed.
* A resource, abc.html, is protected with Form base authentication on host1.mydomain1.com
* A resource, xyz.html, is protected with Basic over LDAP authentication on host2.mydomain2.com.
Following are the steps that explain how multi domain SSO works
1. User initiates a request for a Web page from a browser.
For instance, the request could be for host2.mydomain2/xyz.html.
2. Webgate2 (on host2.domain2.com) sends the authentication request back through the user's browser in search of primary authentication server. In this example you have designated host1.domain1.com to be the primary authentication server.
3. The request for authentication is sent from the user's browser to the primary authentication server, host1.domain1.com.
This request flows to the Access Server. The user logs in with the corresponding authentication scheme and the obSSO cookie is set for host1.domain1.com. The Access Server also generates a session token with a URL that contains the obSSO Cookie.
4. The session token and obSSOCookie are returned to the user’s browser.
5. The session token and obSSOCookie are sent to host2.domain2.com
6. The Web gate (webgate2) on host2.domain2.com sets the obSSOCookie for its own domain (.domain2.com) and satisfies the user’s original request for the resource host2.domain2.com/xyz.html. User gets the resource.
7. On the same browser if user accesses the host1.domain1.com page then resource will be presented without asking credentials as obSSOCookie is already available with .domain1.com (see step 3).
Q: Explain the authentication plugins credential_mapping and validate_password?
A: credential_mapping plugin performs the task of mapping the user credentials to a unique DN in the directory server. WebGate searches the directory server for user profiles matching these attributes. validate_password plugin gets called only after username is validated.
Q: What is an Access Server SDK?
A: The Access Manager Software Developer's Kit (SDK) enables you to enhance the access management capabilities of the Access System. This SDK enables you to create a specialized AccessGate. The Access Manager SDK creates an environment for you to build a dynamic link library or a shared object to perform as an AccessGate. You also need the configureAccessGate.exe tool to verify that your client works correctly.
Q: What is an Identity XML?
A: IdentityXML provides a programmatic interface for carrying out the actions that a user can perform when accessing a COREid application from a browser. For instance, a program can send an IdentityXML request to find members of a group defined in the Group Manager application, or to add a user to the User Manager.
IdentityXML enables you to process simple actions and multi-step workflows to change user, group, and organization object profiles.
After creating the IdentityXML request, you construct a SOAP wrapper to send the IdentityXML request to WebPass using HTTP. The IdentityXML API uses XML over SOAP. We pass IdentityXML parameters to the COREid Server using an HTTP request.This HTTP request contains a SOAP envelope.When WebPass receives the HTTP request, the SOAP envelope indicates that it is an IdentityXML request rather than the usual browser request.
The request is forwarded to the COREid Server, where the request is carried out and a response is returned. Alternatively, you can use WSDL to construct the SOAP request. The SOAP content looks like this, SOAP envelope (with oblix namespace defined), SOAP body (with authentication details), actual request (with application name and params). The application name can be userservcenter, groupservcenter or objservcenter (for organizations).
Q: What is an SSPI connector and its role in Oracle Access Manager integrations?
A: The Security Provider for WebLogic SSPI (Security Provider) ensures that only appropriate users and groups can access Oracle Access Manager-protected WebLogic resources to perform specific operations. The Security Provider also enables you to configure single sign-on between Oracle Access Manager and WebLogic resources.
The WebLogic security framework provides Security Service Provider Interfaces (SSPIs) to protect J2EE applications. The Security Provider takes advantage of these SSPIs, enabling you to use Oracle Access Manager to protect WebLogic resources via:
Authenticator: This security provider uses Oracle Access Manager authentication services to authenticate users who access WebLogic applications. Users are authenticated based on their credentials, such as user name and password.
The security provider also offers user and group management functions. It enables the creation and deletion of users and groups from the BEA WebLogic Server. It also provides single sign-on between WebGates and portals.
Identity Asserter: Like the Authenticator, this security provider uses Oracle Access Manager authentication services to validate already-authenticated Oracle Access Manager users using the ObSSOCookie and to create a WebLogic-authenticated session.
Authorizer: This security provider uses Oracle Access Manager authorization services to authorize users who are accessing a protected resource. The authorization is based on Oracle Access Manager policies.
Role Mapper: This security provider returns security roles for a user. These roles are defined in Oracle Access Manager, and they are provided by Oracle Access Manager using return actions on a special authentication policy. This authentication policy contains a resource with a URL prefix of /Authen/Roles. Role Mapper maps these roles to predefined security roles in WebLogic.
Q: Explain the integration and architecture of OAM-OAAM integration?
A: Using these products in combination will allow you fine control over the authentication process and full capabilities of pre-/post- authentication checking against Adaptive Risk Manager models.
The OAAM’s ASA-OAM integration involves two Oracle Access Manager AccessGates: one for fronting the Web server (a traditional WebGate) to Adaptive Strong Authenticator and one for the embedded AccessGate. The access server SDK to be installed and configureAccessGate tool to be run. The ASA bharosa files to updated with ASDK location. An application to be protected using ASA authentication scheme and to be tested for ASA landing page for login.
Here is how the flow goes:
1. User requests for a resource.
2. Webgate acting in the front end for ASA application will intercept the request and will redirect to the ASA application.
3. The user enter credentials and the Access SDK setup in the ASA application will contact the Access gate which inturn contacts the access server for validating the credentials.
4. Upon successful authentication, access server will generate obSSOCookie and will forwards it to the browser.
5. Then the user will be shown the requested resource.
Q: Explain IWA mechanism in Oracle Access manager?
A: The OAM has a feature which enables Microsoft Internet Explorer users to automatically authenticate to their Web applications using their desktop credentials. This is known as Windows Native Authentication.
Q: Explain various major params defined in webgate instance profile?
A:
A: The Policy Manager API provides an interface which enables custom applications to access the authentication, authorization, and auditing services of the Access Server to create and modify Access System policy domains and their contents.
Q: When do you need an access gate?
A: An access gate is required instead of a standard webgate when you need to control access to a resource where OAM doesnot provide OOTB solution. These might include:
Q: Explain the flow when a user makes a request protected by an access gate (not webgate)?
A: The flow is shown below.
Oracle Identity Federation:
Q: What is Federation?
A: Federation is the user account linking between providers in a circle of trust.
Q: What is Federated Identity?
A: Identity across domains is called Federation. The identity that is federated encircled with trust by linking of one more more accounts with one or more identity and service providers is called Federated Identity.
Q: What is the difference between Multi Domain SSO and Federation?
A: There are couple of differences and are listed below.
Q: What is an Identity Provider and Service Provider?
A: IDP is the site that authenticates the user and sends an assertion to the destination site or SP. SP is the site that consumes the assertion and determines the entitlements of the user and grants or deny access to the requested resource.
Q: Explain the flow when an user makes a federation request?
A:
Step 1: The user logs in to the identity provider using an ID and password for authentication. Once the user is authenticated, a session cookie is placed in the browser.
Step 2: The user then clicks on the link to view an application residing on the service provider. The IdP creates a SAML assertion based on the user’s browser cookie, digitally signs the assertion, and then redirects to the SP.
Step 3: The SP receives the SAML assertion, extracts the user’s identity information, and maps the user to a local user account on the destination site.
Step 4: An authorization check is then performed and if successfully authorized, redirects the user’s browser to the protected resource. If the SP successfully received and validated the user, it will place its own cookie in the user’s browser so the user can now navigate between applications in both domains without additional logins.
Q: What is the authentication mechanism used for federation?
A: Assertions. The assertion created by the IDP will be sent to SP where it will be validated.
Q: Explain how Form login works if the form login page is present in different domain from OAM?
A: The mechanism here is same as how the multi domain SSO works. Importantly, all of the activities for form authentication are carried out between the browser and one web server.
Now, suppose you want to access a resource http://www.B.com/pageB.html but still be authenticated by the login form on www.A.com.
Q: What is auto-learning?
A: Auto-learning is a set of functions in OAAM that profiles behavior. The behavior of users, devices and locations themselves are recorded and used to evaluate current behavior. For example, OAAM can profile a user based on login time. If John logs in between 8am - 10am 87% of the time then the risk level is elevated if he is attempting to login at 2am. In other words he is outside of his normal login time profile.
Q: How does OAAM prevent session-hijacking?
A: To protect against fraudulent transactions occurring over hijacked sessions, Adaptive Strong Authenticator can be easily deployed in session during a sensitive transaction. This requires a human interaction (entering a PIN/OTP/Password on a PinPad/KeyPad) in a process which an automated attack cannot easily navigate using software. For example, the destination account number in a wire transfer transaction could be entered using a PinPad to prevent an automated attack from alerting the account number.
Adaptive Risk Manager offers extensive protections against fraudulent transactions in session. Once a login has cleared our pre-authentication security gateway (computer and location fraud patterns) and has authenticated successfully with the proper credentials, there are still multiple strong security gateways remaining, within the Adaptive Risk Manager model.
Q: How can OAAM prevent phishing?
A: There are a number of anti-phishing features of OAAM. Phishing attacks are often aimed at credential theft. A Phishing site will usually send the users to the real site once they steal their credentials so the user does not suspect anything has gone wrong. When this happens OAAM can recognize that the user is coming from a referral URL not sanctioned by the bank. When OAAM sees this it can add the user to a "phishing victims" group. Membership in this group will increase their risk when attempting transactions such as a wire transfer. As well an investigation case will be created so the referral URL and the user can be evaluated. If all is OK the URL can be white listed and the user removed from the group.
There are also a number of other symptoms of credential theft that OAAM can detect. Factors such as max velocity, device and location usage can be very valuable in determining risk that an access attempt is not from the valid user.
Q: What are different keystores used in OAAM?
A: There are 3 keystores, System, Database and SOAP/WebServices. Encryption of SOAP keystore is optional.
A: Yes, OAAM Admin is a standard web application and uses container provided Authentication out of the box. Since OAAM Admin works with predefined Roles (CSR, CSR Manager so on), the identity store used by OAM should have user & role mappings. The OAAM Admin guide contains these details. Simply assume that OAAM admin console is a generic web application deployed on an application server. And then a customer wants OAM SSO on the admin console. Hence, a web server proxy is needed and then a webgate on the proxy web server and then connector on the app server to perform identity assertion.
This is pretty much standard integration for OAM that we support for any custom application. This case is simply more special because the custom application turns out to be OAAM.
Oracle Identity Manager:
Q: What is user provisioning?
Q: What is reconciliation?
Note: I will be updating this post every now and then. So keep tuned to this.
Q: What is an identity?
A: An identity is a piece of information used to identify an entity whether it is a user or group etc.,.
LDAP:
Q: What is an object class and their different types?
A: An object class specifies set of attributes that are used to define an object.
- Structural. Indicates the attributes that the entry may have and where each entry may occur in the DIT. A Structural object class defines the backbone of an LDAP entry. An entry references a Structural object class as the basis for its required and optional attributes. Eg; inetorgperson, organizationalunit etc., Structural class defines the idenity of an object and Auxiliary object class is used to add attributes. An entry must contain one structual and many auxiliary object classes.
- Auxiliary. Indicates the attributes that the entry may have. Auxiliary object classes allow additional attributes to be "mixed" with a Structural object class. For example, you can add inetOrgPerson as your structural object class and associate it with the tab in the User Manager application. You could then add Auxiliary object classes with special attributes for various types of people, such customers, partners, and so on.
- Abstract. Indicates a "partial" specification in the object class hierarchy; only structural and auxiliary subclasses may appear as entries in the directory.
A:
dn: cn=subschemasubentry
changetype: modify
add: objectclasses
objectclasses: ( 1.2.3.4.5 NAME 'myOC'
DESC 'my Objectclass definition' MAY myAttr )
dn: cn=subschemasubentry
changetype: modify
add: attributetypes
attributetypes: ( 1.2.3.4.5.6.7 NAME "myAttr" DESC "New attribute definition" EQUALITY caseIgnoreMatch
SYNTAX "1.3.6.1.4.1.1466.115.121.1.15" )
dn: cn=person one,dc=example,dc=com
changetype: modify
add: myAttr
myAttr: myattrValue1
dn: cn=person one,dc=example,dc=com
changetype: modify
add: objectclass
objectclass: myOC
Adding an Auxiliary object class to a schema:
objectclass ( 1.3.6.1.4.1.6863.2.4.57 NAME 'ourObject' DESC 'A very useful object' SUP top AUXILIARY MUST ( dohicky $ gobbledegook ) MAY ageAtBirth )
Adding auxiliary object class to an existing entry:dn: cn=user1,dc=example,dc=com
changetype: modify
add: objectclasses
objectclasses:inetorgperson
objectclasses: myAuxOC
Q: What is DN and RDN?
A: A DN is the LDAP entry that uniquely identifies and describes the entry in LDAP server.
cn=Jones,dc=oracle,dc=com is the DN of user Jones and RDN is cn=Jones.
Q: How do you define Identity Management & Access Management?
A: Identity Management enables customers to manage end-to-end lifecycle of user identities across all enterprise resources securely. Access Management provides web access management including authentication, fine grained authorization, federation and proactive online fraud prevention.
Q:What are various domains that fall under identity management?
A: Identity Management, Access Management, Directory Management. Oracle Products that fall under Identity Management are Oracle Identity Manager and Oracle Role Manager. Oracle products that fall under Access Management are Oracle Access Manager, Oracle Entitlement Server, Oracle Adaptive Access Manager, Oracle Identity federation and Enterprise Single Sign-On. Oracle products that fall under Directory Management are OID and OVD.
Oracle Access Manager:
Oracle Access Manager is a state-of-the-art solution for both centralized identity management and access control, providing an integrated standards-based solution that delivers authentication, web single sign-on, access policy creation and enforcement, user self-registration and self-service, delegated administration, reporting, and auditing.
Q: What is Single Sign On?
A: Single Sign-On allows users to sign on once to a protected application and gain access to the other protected resources within the same domain defined with same authentication level.
Q: What is multi domain Single Sign-On?
A: Multi Domain SSO gives users the ability to access more than one protected resource (URL and Applications), which are scattered across multiple domains with one time authentication.
Q: What is the authentication mechanism used by Oracle Access Manager?
A: ObSSOCookie and it is stateless.
Q: Explain various security modes present in Oracle Access Manager?
A:
Open: Allows unencrypted communication. In Open mode, there is no authentication or encryption between the AccessGate and Access Server. The AccessGate does not ask for proof of the Access Server's identity and the Access Server accepts connections from all AccessGates. Similarly, Identity Server does not require proof of identity from WebPass.
Simple: Supports encryption by Oracle. In Simple mode communications between Web clients (WebPass and Identity Server, Policy Manager and WebPass, and Access Server and WebGate are encrypted using TLS v1. In both Simple and Cert mode, Oracle Access Manager components use X.509 digital certificates only. This includes Cert Authentication between WebGates and the Access Server where the standard cert-decode plug-in decodes the certificate and passes certificate information to the standard credential_mapping authentication plug-in. For each public key there exists a corresponding private key that Oracle Access Manager stores in the aaa_key.pem file for the Access Server (or ois_key.pem for Identity Server).
Cert: Requires a third-party certificate. Use Cert (SSL) mode if you have an internal Certificate Authority (CA) for processing server certificates. In Cert mode, communication between WebGate and Access Server, and Identity Server and WebPass are encrypted using Transport Layer Security, RFC 2246 (TLS v1).
Q: Explain the architecture of Oracle Access Manager?
A: Oracle Access Manager architecture mainly consists for components such as Identity Server, WebPass, Policy Manager, Access Server and a WebGate. Identity Server is a standalone C++ server which communicates directly with LDAP.
It also receives requests and sends response to Webpass. WebPass is a web server plugin that passes info between identity server and webserver. It redirects HTTP requests from browser to Access Server, and sends Identity XML SOAP requests to Identity Server.
Policy Manager (PMP or PAP) is a web server plugin that communicates directly with user, configuration and policy repositories. Access Server is a stand alone C++ server and is also called PDP. It receives requests from & sends responses to WebGates/AccessGates.
It also communicates with LDAP. It answers Access Server SDK requests. WebGate (PEP) is a web server plugin that passes info between webserver and access server. It passes user authentication data to access server for processing.
Q: What are the ObSSOCookie Contents?
A: Cookie contains encrypted session token and non-encrypted data.
This Encrypted Session Token consists of : DN of the authenticated user, level of auth scheme, ip address of client to which cookie was issued, time the cookie is issued, time the cookie was last updated. If the user is not idle, then cookie will get automatically updated at a fixed interval to prevent session timeout. The updated interval is the 1/4 th of idle session timeout of accessgate.
The Unencrypted ObSSOCookie data contains cookie expiry time, domain in which cookie is valid, additional flag that determines if cookie can only be sent using SSL.
Q: What is the key used for encrypting the ObSSOCookie?
A: Shared Secret key. It is configured in the Identity Admin console and can be generated by the OAM administrator.
Q: What happens if the ObSSOCookie is tampered?
A: When access system generates ObSSOCookie, MD-5 hash is taken from session token. So when the user is authenticated again using the cookie, the MD5 hash is compared with original cookie contents. MD-5 hash is a one-way hash, hence it cant be unencrypted. Access server compares the cookie contents with hash. If both are not same, then cookie is tampered in the interim. This cookie does not contain username and password.
Q: What is the difference between WebGate and AccessGate?
A: WebGate is an out-of-the-box plug-in that intercepts Web resource (HTTP) requests and forwards them to the Access Server for authentication and authorization. An AccessGate is a custom webgate that can intercept requests of HTTP and non-HTTP resources.
Q: What are the major parameters defined in an authentication scheme?
A: The authentication scheme level which defines the level of the security defined for an application.
Q: Explain the flow when a user requests for an application protected by Oracle Access Manager?
A: The following steps describes the flow when a user makes a request to access a resource protected by the Oracle Access Manager.
- User requests for a resource through a web browser.
- The Webgate intercepts the requests and checks with the Access Server whether the resource is protected or not.
- If the resource is not protected, then the user will be shown the requested resource.
- If the resource is protected, then Access Server will check with policy manager the authentication scheme configured for that resource.
- User will be prompted to enter their credentials as per the auth scheme defined for the resource.
- Webgate will send the credentials to the Access Server to check it against the backend (LDAP server).
- Upon successful authentication, Access server checks whether the user is authorized to access the resource or not.
- If the user is authorized, then the Access Server will create the session id and passes it to the webgate. An ObSSOCookie is created and will be sent to the user browser and the user will be shown the requested resource.
- If the user is not authorized, then an error page (if its defined in policy domain) will be shown to the user.
A: Multi Domain SSO gives users the ability to access more than one protected resource (URL and Applications), which are scattered across multiple domains with one time authentication.
- For multi domain SSO to work, Access Servers in all domains must use same policy directory.
- Multi domain works only with web gates, not Access Gates.
- Within each individual domain, each web gate must have same “primary HTTP cookie domain”.
Lets assume that OAM components are installed in host1.domain1.com and we will designate host1.domain1.com as the primary authentication server.
* Host2.domain2.com with web gate (ex: webgate2) installed.
* A resource, abc.html, is protected with Form base authentication on host1.mydomain1.com
* A resource, xyz.html, is protected with Basic over LDAP authentication on host2.mydomain2.com.
Following are the steps that explain how multi domain SSO works
1. User initiates a request for a Web page from a browser.
For instance, the request could be for host2.mydomain2/xyz.html.
2. Webgate2 (on host2.domain2.com) sends the authentication request back through the user's browser in search of primary authentication server. In this example you have designated host1.domain1.com to be the primary authentication server.
3. The request for authentication is sent from the user's browser to the primary authentication server, host1.domain1.com.
This request flows to the Access Server. The user logs in with the corresponding authentication scheme and the obSSO cookie is set for host1.domain1.com. The Access Server also generates a session token with a URL that contains the obSSO Cookie.
4. The session token and obSSOCookie are returned to the user’s browser.
5. The session token and obSSOCookie are sent to host2.domain2.com
6. The Web gate (webgate2) on host2.domain2.com sets the obSSOCookie for its own domain (.domain2.com) and satisfies the user’s original request for the resource host2.domain2.com/xyz.html. User gets the resource.
7. On the same browser if user accesses the host1.domain1.com page then resource will be presented without asking credentials as obSSOCookie is already available with .domain1.com (see step 3).
Q: Explain the authentication plugins credential_mapping and validate_password?
A: credential_mapping plugin performs the task of mapping the user credentials to a unique DN in the directory server. WebGate searches the directory server for user profiles matching these attributes. validate_password plugin gets called only after username is validated.
Q: What is an Access Server SDK?
A: The Access Manager Software Developer's Kit (SDK) enables you to enhance the access management capabilities of the Access System. This SDK enables you to create a specialized AccessGate. The Access Manager SDK creates an environment for you to build a dynamic link library or a shared object to perform as an AccessGate. You also need the configureAccessGate.exe tool to verify that your client works correctly.
Q: What is an Identity XML?
A: IdentityXML provides a programmatic interface for carrying out the actions that a user can perform when accessing a COREid application from a browser. For instance, a program can send an IdentityXML request to find members of a group defined in the Group Manager application, or to add a user to the User Manager.
IdentityXML enables you to process simple actions and multi-step workflows to change user, group, and organization object profiles.
After creating the IdentityXML request, you construct a SOAP wrapper to send the IdentityXML request to WebPass using HTTP. The IdentityXML API uses XML over SOAP. We pass IdentityXML parameters to the COREid Server using an HTTP request.This HTTP request contains a SOAP envelope.When WebPass receives the HTTP request, the SOAP envelope indicates that it is an IdentityXML request rather than the usual browser request.
The request is forwarded to the COREid Server, where the request is carried out and a response is returned. Alternatively, you can use WSDL to construct the SOAP request. The SOAP content looks like this, SOAP envelope (with oblix namespace defined), SOAP body (with authentication details), actual request (with application name and params). The application name can be userservcenter, groupservcenter or objservcenter (for organizations).
Q: What is an SSPI connector and its role in Oracle Access Manager integrations?
A: The Security Provider for WebLogic SSPI (Security Provider) ensures that only appropriate users and groups can access Oracle Access Manager-protected WebLogic resources to perform specific operations. The Security Provider also enables you to configure single sign-on between Oracle Access Manager and WebLogic resources.
The WebLogic security framework provides Security Service Provider Interfaces (SSPIs) to protect J2EE applications. The Security Provider takes advantage of these SSPIs, enabling you to use Oracle Access Manager to protect WebLogic resources via:
- User authentication
- User authorization
- Role mapping
Authenticator: This security provider uses Oracle Access Manager authentication services to authenticate users who access WebLogic applications. Users are authenticated based on their credentials, such as user name and password.
The security provider also offers user and group management functions. It enables the creation and deletion of users and groups from the BEA WebLogic Server. It also provides single sign-on between WebGates and portals.
Identity Asserter: Like the Authenticator, this security provider uses Oracle Access Manager authentication services to validate already-authenticated Oracle Access Manager users using the ObSSOCookie and to create a WebLogic-authenticated session.
Authorizer: This security provider uses Oracle Access Manager authorization services to authorize users who are accessing a protected resource. The authorization is based on Oracle Access Manager policies.
Role Mapper: This security provider returns security roles for a user. These roles are defined in Oracle Access Manager, and they are provided by Oracle Access Manager using return actions on a special authentication policy. This authentication policy contains a resource with a URL prefix of /Authen/Roles. Role Mapper maps these roles to predefined security roles in WebLogic.
Q: Explain the integration and architecture of OAM-OAAM integration?
A: Using these products in combination will allow you fine control over the authentication process and full capabilities of pre-/post- authentication checking against Adaptive Risk Manager models.
The OAAM’s ASA-OAM integration involves two Oracle Access Manager AccessGates: one for fronting the Web server (a traditional WebGate) to Adaptive Strong Authenticator and one for the embedded AccessGate. The access server SDK to be installed and configureAccessGate tool to be run. The ASA bharosa files to updated with ASDK location. An application to be protected using ASA authentication scheme and to be tested for ASA landing page for login.
Here is how the flow goes:
1. User requests for a resource.
2. Webgate acting in the front end for ASA application will intercept the request and will redirect to the ASA application.
3. The user enter credentials and the Access SDK setup in the ASA application will contact the Access gate which inturn contacts the access server for validating the credentials.
4. Upon successful authentication, access server will generate obSSOCookie and will forwards it to the browser.
5. Then the user will be shown the requested resource.
Q: Explain IWA mechanism in Oracle Access manager?
A: The OAM has a feature which enables Microsoft Internet Explorer users to automatically authenticate to their Web applications using their desktop credentials. This is known as Windows Native Authentication.
- user logs in to the desktop machine, and local authentication is completed using the Windows Domain Administrator authentication scheme.
- The user opens an Internet Explorer (IE) browser and requests an Access System-protected Web resource.
- The browser notes the local authentication and sends a token to the IIS Web server.
- The IIS Web server uses the token to authenticate the user and set up the REMOTE_USER HTTP header variable that specifies the user name supplied by the client and authenticated by the server.
- The WebGate installed on the IIS Web server uses the hidden feature of external authentication to get the REMOTE_USER header variable value and map it to a DN for the ObSSOCookie generation and authorization.
- The WebGate creates an ObSSOCookie and sends it back to the browser.
- The Access System authorization and other processes proceed as usual.
The maximum session timeout period configured for the WebGate is applicable to the generated ObSSOCookie.
Q: Explain various major params defined in webgate instance profile?
A:
- Hostname: name of the machine hosting the access gate.
- Maximum User Session Time: Maximum amount of time in seconds that a user's authentication session is valid, regardless of their activity. At the expiration of this session time, the user is re-challenged for authentication. This is a forced logout. Default = 3600. A value of 0 disables this timeout setting.
- Idle Session Time (seconds): Amount of time in seconds that a user's authentication session remains valid without accessing any AccessGate protected resources.
- Maximum Connections: Maximum number of connections this AccessGate can establish. This parameter is based on how many Access Server connections are defined to each individual Access Server. This number may be greater than the number allocated at any given time.
- IPValidationException: IPValidationException is specific to WebGates. This is a list of IP addresses that are excluded from IP address validation. It is often used for excluding IP addresses that are set by proxies.
- Maximum Client Session Time :Connection maintained to the Access Server by the AccessGate. If you are deploying a firewall (or another device) between the AccessGate and the Access Server, this value should be smaller than the timeout setting for the firewall.
- Failover Threshold: Number representing the point when this AccessGate opens connections to Secondary Access Servers. If you type 30 in this field, and the number of connections to primary Access Servers falls to 29, this AccessGate opens connections to secondary Access Servers.
- Preferred HTTP Host : Defines how the host name appears in all HTTP requests as they attempt to access the protected Web server. The host name in the HTTP request is translated into the value entered into this field regardless of the way it was defined in a user's HTTP request.
- Primary HTTP Cookie Domain: This parameter describes the Web server domain on which the AccessGate is deployed, for instance, .mycompany.com.
- IPValidation: IP address validation is specific to WebGates and is used to determine whether a client's IP address is the same as the IP address stored in the ObSSOCookie generated for single sign-on.
A: The Policy Manager API provides an interface which enables custom applications to access the authentication, authorization, and auditing services of the Access Server to create and modify Access System policy domains and their contents.
Q: When do you need an access gate?
A: An access gate is required instead of a standard webgate when you need to control access to a resource where OAM doesnot provide OOTB solution. These might include:
- protection for non-http resources (EJB, JNDI etc.,)
- Implementation of SSO to protect a combination of http and non-http resources.
Q: Explain the flow when a user makes a request protected by an access gate (not webgate)?
A: The flow is shown below.
- The application or servlet containing the access gate code receives resource request from the user.
- The access gate code constructs ObResourceRequest structure and access gate contacts Access server to find whether resource is protected or not.
- The access server responds.
- If the resource is not protected, access gate allows user to access the resource. Otherwise..,
- Access Gate constructs ObAuthenticationScheme structure to ask Access Server what credentials the user needs to supply.
- The access server responds.
- The application uses a form or some other means to fetch the credentials.
- The AccessGate constructs ObUserSession structure which presents user details to Acc Server.
- If credentials are proven valid, access gate creates a session token for the user and then sends an authorization request to the access server.
- Access server validates if the user is authz to access that resource.
- Access gate allows user to access the requested resource.
Oracle Identity Federation:
Q: What is Federation?
A: Federation is the user account linking between providers in a circle of trust.
Q: What is Federated Identity?
A: Identity across domains is called Federation. The identity that is federated encircled with trust by linking of one more more accounts with one or more identity and service providers is called Federated Identity.
Q: What is the difference between Multi Domain SSO and Federation?
A: There are couple of differences and are listed below.
- Multi domain SSO can happen if the applications are residing in different domains within same organization or a company. Federation happens if the applications are residing within same organization as well as between organizations.
- In Federation, there is a trust established between both the providers residing in different domains, whereas in Multi Domain SSO, trust is not established.
- The mechanism used in MD - SSO is cookie and is SAML Assertion in case of Federation.
- The attributes passed in the header cannot be encrypted OOTB in MD-SSO where as it can be digitally signed.
- There is more of security involved along with interoperability in case of federation.
Q: What is an Identity Provider and Service Provider?
A: IDP is the site that authenticates the user and sends an assertion to the destination site or SP. SP is the site that consumes the assertion and determines the entitlements of the user and grants or deny access to the requested resource.
Q: Explain the flow when an user makes a federation request?
A:
Step 1: The user logs in to the identity provider using an ID and password for authentication. Once the user is authenticated, a session cookie is placed in the browser.
Step 2: The user then clicks on the link to view an application residing on the service provider. The IdP creates a SAML assertion based on the user’s browser cookie, digitally signs the assertion, and then redirects to the SP.
Step 3: The SP receives the SAML assertion, extracts the user’s identity information, and maps the user to a local user account on the destination site.
Step 4: An authorization check is then performed and if successfully authorized, redirects the user’s browser to the protected resource. If the SP successfully received and validated the user, it will place its own cookie in the user’s browser so the user can now navigate between applications in both domains without additional logins.
Q: What is the authentication mechanism used for federation?
A: Assertions. The assertion created by the IDP will be sent to SP where it will be validated.
Q: Explain how Form login works if the form login page is present in different domain from OAM?
A: The mechanism here is same as how the multi domain SSO works. Importantly, all of the activities for form authentication are carried out between the browser and one web server.
Now, suppose you want to access a resource http://www.B.com/pageB.html but still be authenticated by the login form on www.A.com.
- The authentication scheme required by pageB needs to have a redirect URL set to http://www.A.com.
- The WebGate at www.B.com redirects you to the NetPoint URL obrareq.cgi on www.A.com, with a query string that contains the original request (wu and wh).
- The WebGate on www.A.com will determine that you need to do a form login for that resource, so it will set the ObFormLoginCookie with the wu and wh values from the query string, but will set the ru field to /obrareq.cgi. WebGate on A then redirects your browser to the login form on A.
- When you post your credentials back to A, the ObFormLoginCookie is set back. WebGate on A authenticates your userid and password, sets the ObSSOCookie for the .A.com domain and redirects you back to the ru value from the ObFormLoginCookie, which is /obrareq.cgi.
- This time when your browser requests http://www.A.com/obrareq.cgi, it will pass the ObSSOCookie.
- WebGate will then redirect your browser back to the B webserver, http://www.B.com/obrar.cgi, with the cookie value and the original URL in the query string.
- The WebGate on www.B.com will extract the cookie value and set the ObSSOCookie for domain .B.com, and finally redirect you to http://www.B.com/pageB.html that you originally requested.
Q: What is auto-learning?
A: Auto-learning is a set of functions in OAAM that profiles behavior. The behavior of users, devices and locations themselves are recorded and used to evaluate current behavior. For example, OAAM can profile a user based on login time. If John logs in between 8am - 10am 87% of the time then the risk level is elevated if he is attempting to login at 2am. In other words he is outside of his normal login time profile.
Q: How does OAAM prevent session-hijacking?
A: To protect against fraudulent transactions occurring over hijacked sessions, Adaptive Strong Authenticator can be easily deployed in session during a sensitive transaction. This requires a human interaction (entering a PIN/OTP/Password on a PinPad/KeyPad) in a process which an automated attack cannot easily navigate using software. For example, the destination account number in a wire transfer transaction could be entered using a PinPad to prevent an automated attack from alerting the account number.
Adaptive Risk Manager offers extensive protections against fraudulent transactions in session. Once a login has cleared our pre-authentication security gateway (computer and location fraud patterns) and has authenticated successfully with the proper credentials, there are still multiple strong security gateways remaining, within the Adaptive Risk Manager model.
Q: How can OAAM prevent phishing?
A: There are a number of anti-phishing features of OAAM. Phishing attacks are often aimed at credential theft. A Phishing site will usually send the users to the real site once they steal their credentials so the user does not suspect anything has gone wrong. When this happens OAAM can recognize that the user is coming from a referral URL not sanctioned by the bank. When OAAM sees this it can add the user to a "phishing victims" group. Membership in this group will increase their risk when attempting transactions such as a wire transfer. As well an investigation case will be created so the referral URL and the user can be evaluated. If all is OK the URL can be white listed and the user removed from the group.
There are also a number of other symptoms of credential theft that OAAM can detect. Factors such as max velocity, device and location usage can be very valuable in determining risk that an access attempt is not from the valid user.
Q: What are different keystores used in OAAM?
A: There are 3 keystores, System, Database and SOAP/WebServices. Encryption of SOAP keystore is optional.
- System Keystore: Used for encrypting properties and other non-db related data
- Database: VCryptPassword and Transaction tables. Containing data such as password, PIN, Transaction data (like credit card #, etc)...
- SOAP/WebServices: On the client side to authenticate Web Services request
A: Yes, OAAM Admin is a standard web application and uses container provided Authentication out of the box. Since OAAM Admin works with predefined Roles (CSR, CSR Manager so on), the identity store used by OAM should have user & role mappings. The OAAM Admin guide contains these details. Simply assume that OAAM admin console is a generic web application deployed on an application server. And then a customer wants OAM SSO on the admin console. Hence, a web server proxy is needed and then a webgate on the proxy web server and then connector on the app server to perform identity assertion.
This is pretty much standard integration for OAM that we support for any custom application. This case is simply more special because the custom application turns out to be OAAM.
Oracle Identity Manager:
Q: What is user provisioning?
Q: What is reconciliation?
Note: I will be updating this post every now and then. So keep tuned to this.
Labels:
IDM Questions,
Oracle Identity Management
Subscribe to:
Comments (Atom)